Web security is critical in 2026. With +300% XSS attacks in 2024, GDPR fines up to €20M, and daily data breaches, securing your web applications is no longer optional. This guide covers OWASP Top 10 vulnerabilities, Headless architecture for isolation, and professional tools used at VOID to audit and protect platforms.
🚨 Why Web Security is Critical?
- 🔴 +300% XSS attacks in 2024 (OWASP report)
- 💰 GDPR/CNDP fines: up to €20M or 4% revenue
- 📉 Lost trust: 60% customers leave after breach
- 🏦 Banking compliance: PCI-DSS, ISO 27001 requirements
- ⚖️ Legal liability: DPO, CNDP treatment registry
🎯 XSS (Cross-Site Scripting): Threat #1
XSS (Cross-Site Scripting) is a vulnerability allowing injection of malicious JavaScript code into a web page, executed by victims' browsers. Most prevalent web vulnerability (OWASP Top 10 #3).
XSS Protection with Modern Frameworks
Modern frameworks (Drupal/Twig, Symfony, Laravel, React) provide automatic output escaping by default, drastically reducing XSS risks.
🛡️ Framework Auto-Escape
// ✅ Drupal/Twig (auto-escape enabled)
{{ user_input }} {# Automatic escaping #}
{{ user_input|raw }} {# ❌ Dangerous, avoid! #}
// ✅ Symfony/Twig
{{ form.name }} {# Automatic escaping #}
// ✅ Laravel/Blade
{{ $userInput }} {{-- Automatic escaping --}}
{!! $userInput !!} {{-- ❌ Dangerous, avoid! --}}
// ✅ React (Next.js)
<div>{userInput}</div> {/* Automatic escaping */}
<div dangerouslySetInnerHTML={{__html: userInput}} /> {/* ❌ Dangerous */}XSS Types
1️⃣ Reflected XSS
Payload in URL, executed immediately. Victim clicks malicious link.
2️⃣ Stored XSS
Payload in database, executed for every visitor. More dangerous (persistent).
3️⃣ DOM XSS
Client-side DOM manipulation. No server interaction.
🛡️ OWASP Top 10 (2021): Critical Vulnerabilities
🏗️ Headless Architecture: Security by Isolation
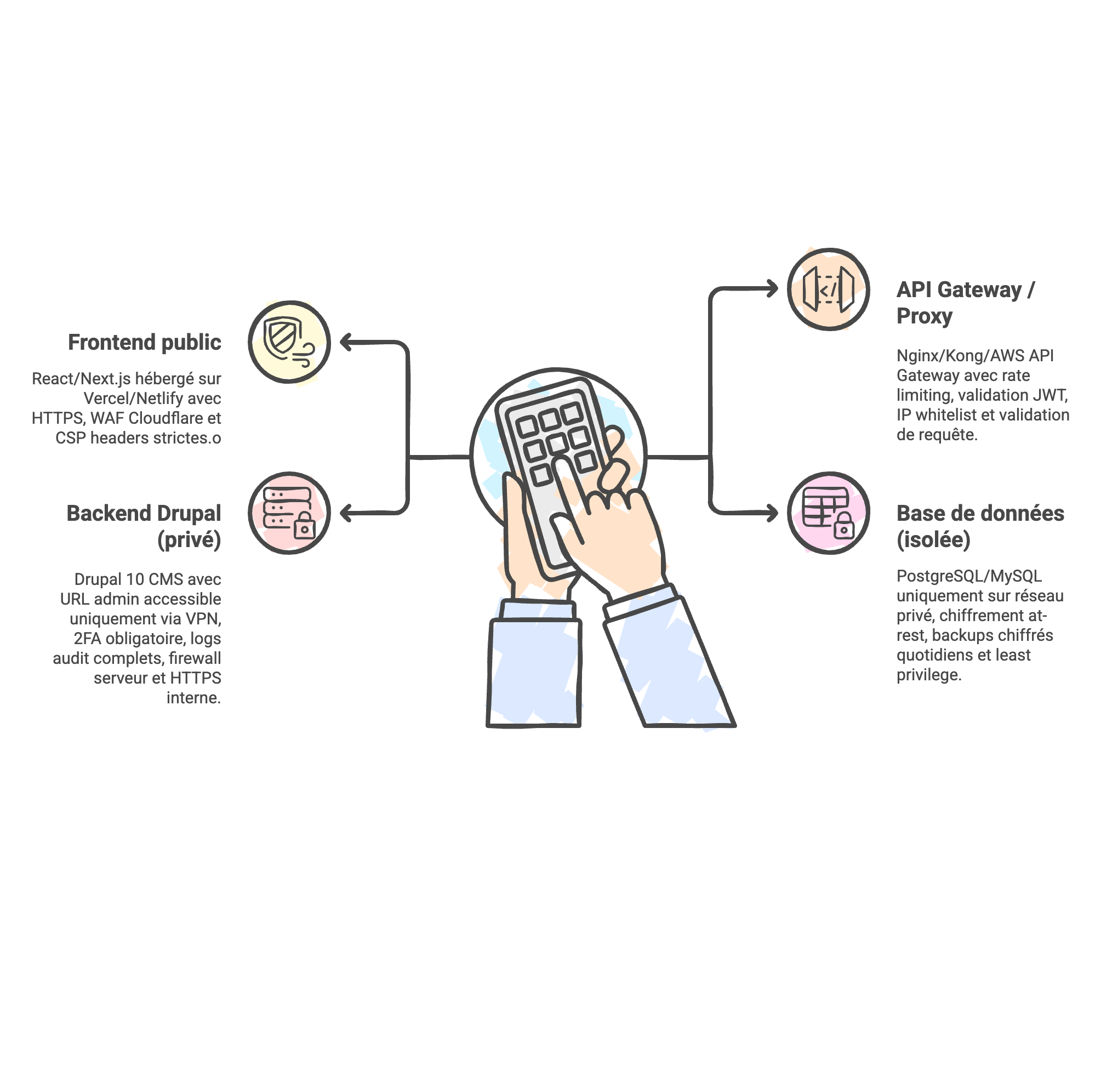
4-layer architecture: Public Frontend (CDN) → API Gateway → Drupal Backend (VPN) → Isolated Database
Headless architecture (separate backend CMS from frontend) provides reinforced security by isolation. Drupal backoffice is physically separated from public React/Next.js frontend.
| Layer | Technologies | Security |
|---|---|---|
| 🌐 Public Frontend | React/Next.js (SSG) • Vercel/Netlify (CDN) • HTTPS (Let's Encrypt) | • WAF Cloudflare (DDoS, XSS) • Strict CSP headers • Static (no PHP) |
| 🔌 API Gateway | Nginx / Kong • Rate limiting • JWT validation | • 100 req/min max • IP whitelist (admin) • Request validation |
| 🔒 Drupal Backend | Drupal 10 CMS • VPN only • Internal HTTPS | • Mandatory 2FA • Audit logs (Watchdog) • Firewall UFW/iptables |
| 🗄️ Database | PostgreSQL / MySQL • Private network • TLS 1.3 | • At-rest encryption (LUKS) • Encrypted backups • Read-only user (API) |
🔑 Headless Architecture Security Benefits
1. Compromised frontend
→ Database unreachable (isolated private network)
2. Frontend XSS attack
→ No admin session access (VPN required)
3. Frontend DDoS
→ Backend protected (Cloudflare CDN absorbs)
4. Admin brute force
→ VPN + 2FA required (admin.void.ma)
5. SQL injection API
→ Prepared statements (Symfony/Doctrine) + read-only user
🔧 Professional Security Tools Used at VOID
🛡️ Acunetix (Vulnerability Scanner)
Market-leading automated scanner. Detects XSS, SQL injection, CSRF, file inclusion, XXE, SSRF, and 7000+ vulnerabilities.
- ✓ Monthly automated scans of banking platforms
- ✓ Stored XSS detection (comments, user profiles)
- ✓ Authentication testing (brute force, session fixation)
- ✓ PCI-DSS compliance reports
🔥 Burp Suite Professional (Manual Pentest)
Essential pentest tool. HTTP proxy, scanner, intruder, repeater, decoder. Advanced manual testing.
- ✓ REST API penetration testing (request tampering)
- ✓ Authentication bypass (JWT manipulation)
- ✓ Business logic flaws detection
- ✓ Parameter fuzzing (advanced injection)
🦅 OWASP ZAP Proxy (Open-Source)
Open-source alternative to Burp Suite. Automatic + manual scanner, HTTP/HTTPS proxy, fuzzer, spider.
- ✓ CI/CD integration (ZAP Docker, automated scans)
- ✓ Baseline scans before deployment
- ✓ Authenticated testing (admin sessions)
- ✓ Ajax spider (React/Vue applications)
🕷️ Netsparker (Reduced False Positives)
Premium scanner with ultra-low false positive rate. Automatic Proof-of-Exploit.
💉 XSSer (XSS Exploitation)
Specialized XSS tool. Automatic detection of reflected, stored, DOM-based XSS. Advanced payloads.
📂 Dirbuster / Gobuster (Directory Enumeration)
Directory bruteforce. Discovery of hidden files/folders (backups, admin panels, config).
✅ Web Security Checklist
🔐 Authentication & Sessions
- ☐ Hashed passwords (bcrypt, Argon2, min 12 chars)
- ☐ 2FA enabled (TOTP, SMS)
- ☐ Rate limiting login (max 5 attempts/min)
- ☐ Session timeout (15min inactivity)
- ☐ HttpOnly + Secure cookies
🛡️ XSS Protection
- ☐ Output encoding (htmlspecialchars)
- ☐ CSP headers configured
- ☐ X-XSS-Protection: 1; mode=block
- ☐ Server-side input validation
- ☐ HTML sanitization (DOMPurify)
💉 Injection Protection
- ☐ Prepared statements (PDO, ORM)
- ☐ Input validation (whitelist)
- ☐ Escape shell commands
- ☐ LDAP injection protection
- ☐ NoSQL injection (MongoDB sanitize)
🔒 HTTPS & Crypto
- ☐ HTTPS mandatory (HSTS)
- ☐ TLS 1.3 minimum
- ☐ Valid certificate (Let's Encrypt)
- ☐ Forward secrecy (ECDHE)
- ☐ Encrypted data at-rest
🎯 Conclusion: Security = Investment, Not Cost
Web Security: Critical in 2025
With +300% XSS attacks, €20M GDPR fines, and daily breaches, investing in security is critical. Headless architecture + professional tools = robust protection.
Need a Professional Security Audit?
VOID performs complete security audits with Acunetix, Burp Suite, ZAP Proxy. Manual + automated penetration testing, detailed report, remediation support.
Request Free Security Audit